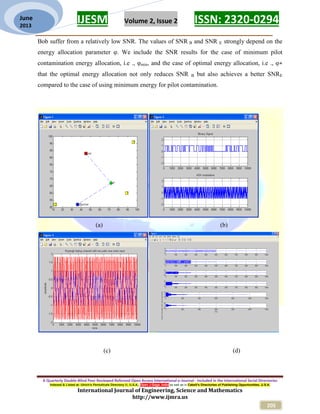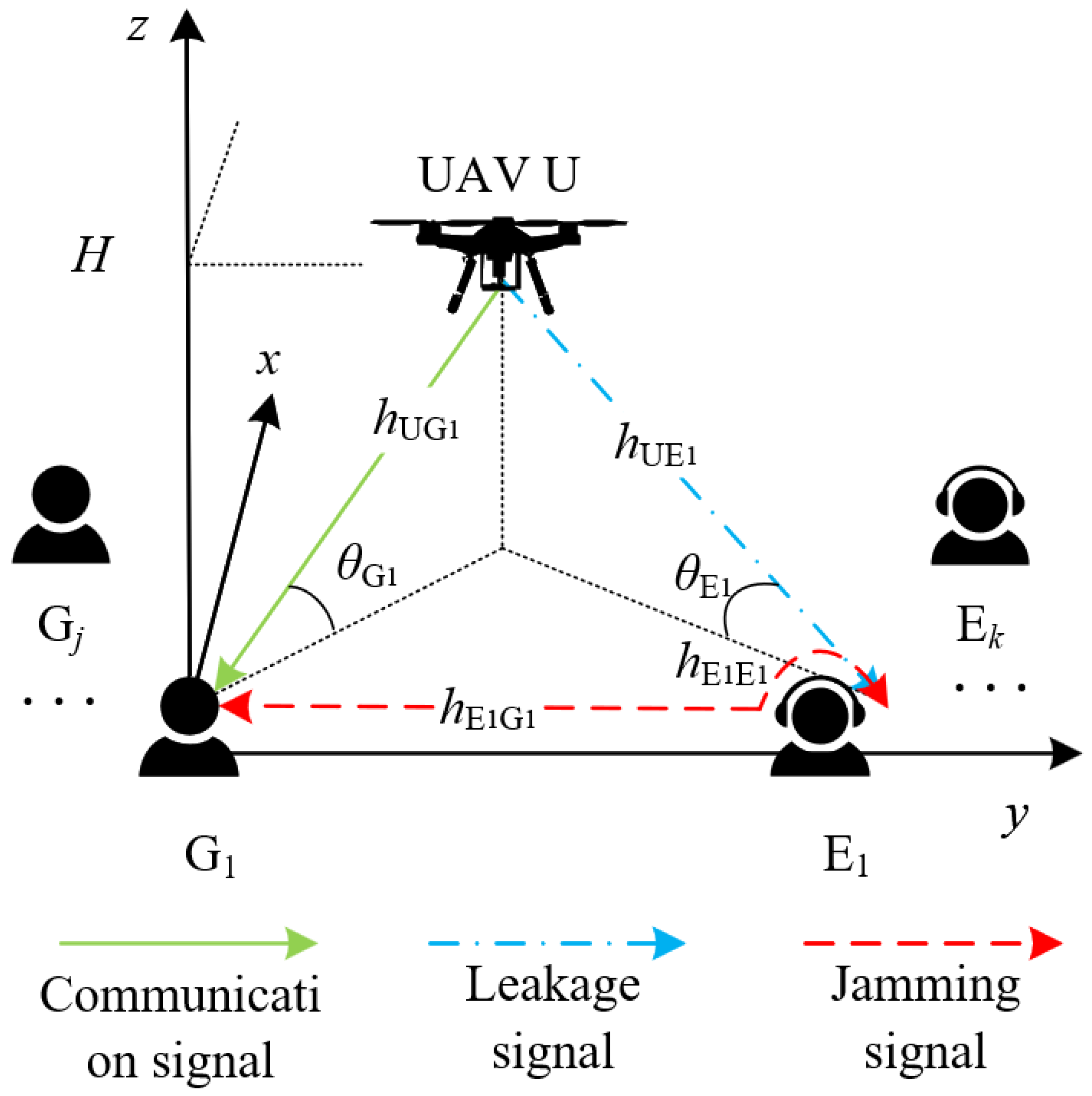
Drones | Free Full-Text | Safeguarding UAV Networks against Active Eavesdropping: An Elevation Angle-Distance Trade-Off for Secrecy Enhancement

Tech vansh - What is an Eavesdropping Attack? #ethicalhacking #hacking #kalilinux #cybersecurity #hackers #hack #hacker #linux #python #anonymous #technology #programming #security #infosec #ethicalhacker #developer #malware #pentesting #web #hacked ...

An illustration of active eavesdropping in massive MIMO-based systems. | Download Scientific Diagram

Electronics | Free Full-Text | Active Eavesdropping Detection Based on Large-Dimensional Random Matrix Theory for Massive MIMO-Enabled IoT

On Eavesdropping Attacks in Wireless Sensor Networks with Directional Antennas - Hong-Ning Dai, Qiu Wang, Dong Li, Raymond Chi-Wing Wong, 2013
MITM attack. Man in the middle cyberattack, active eavesdropping example and unprivate online communication vector Illustration Stock Vector Image & Art - Alamy

Analysis and Validation of Active Eavesdropping Attacks in Passive FHSS RFID Systems | Semantic Scholar

Mini Small Infrared Detecting Night Viewing Video Camera Detector Equipment Tool,active Alarm, Real-time Monitoring,anti-eavesdropping Detector, Anti- | Fruugo NO