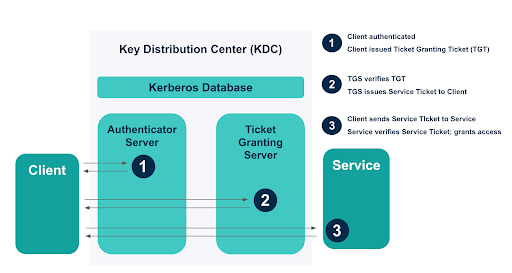
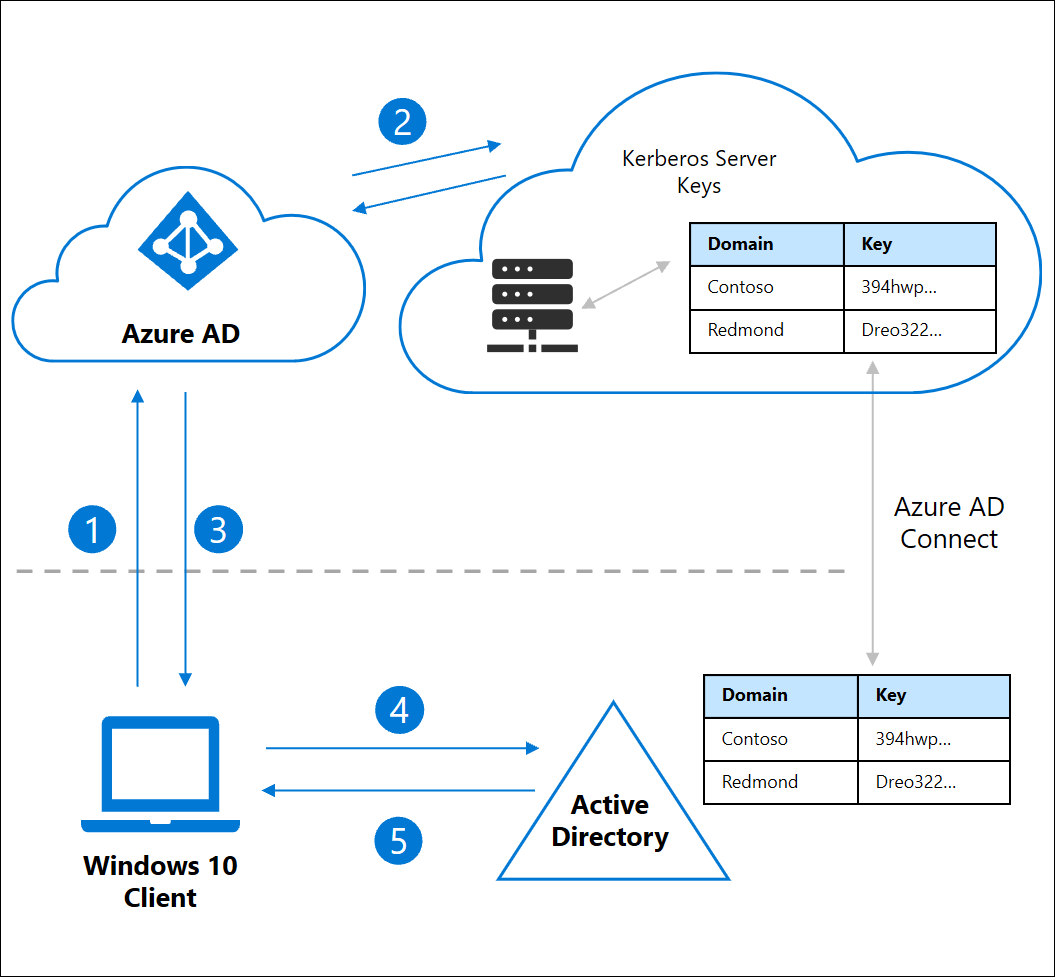
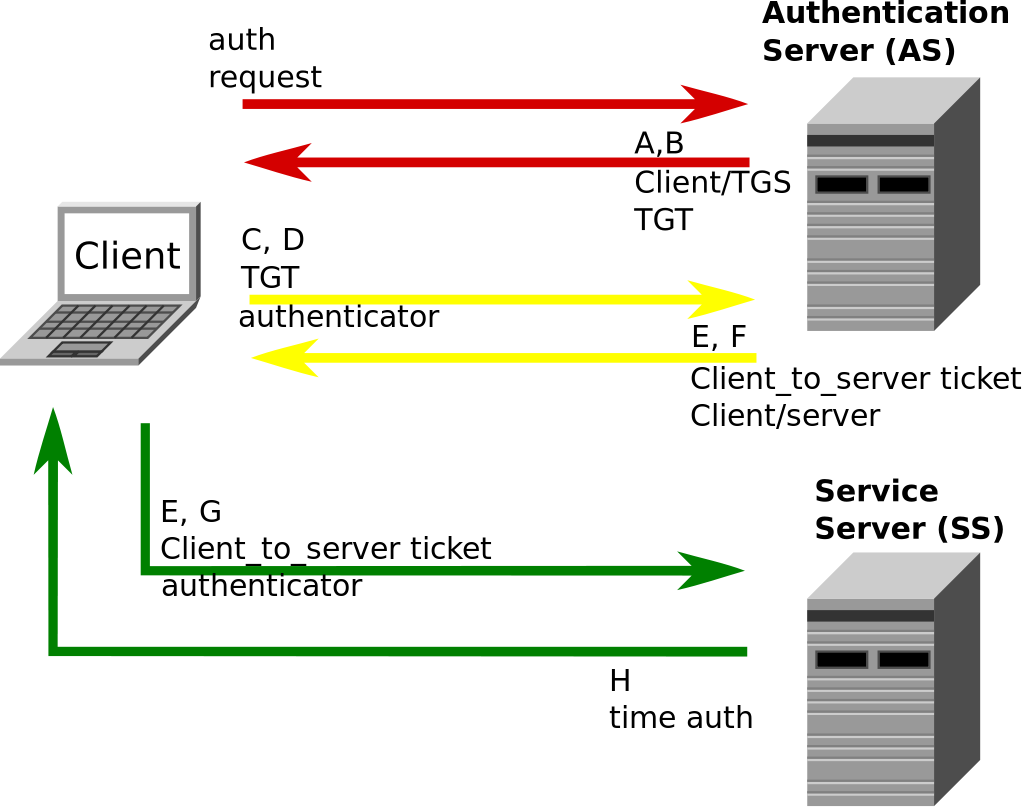
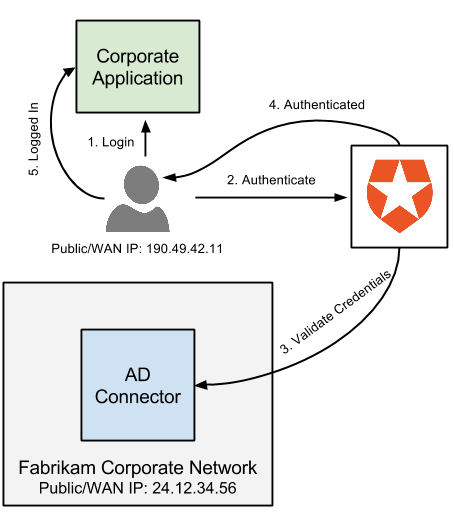
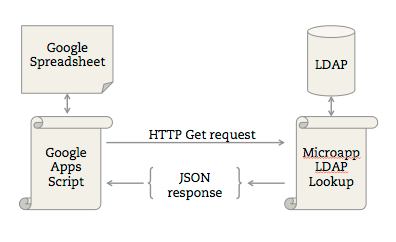
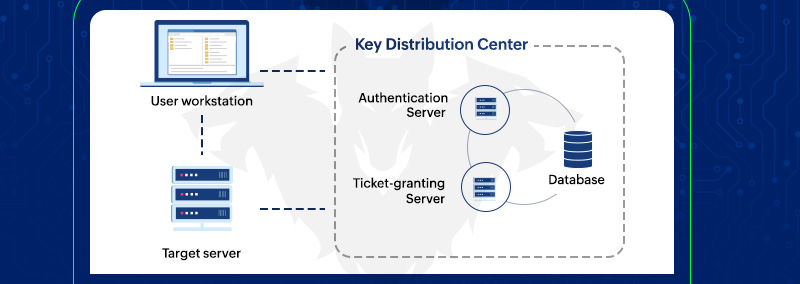
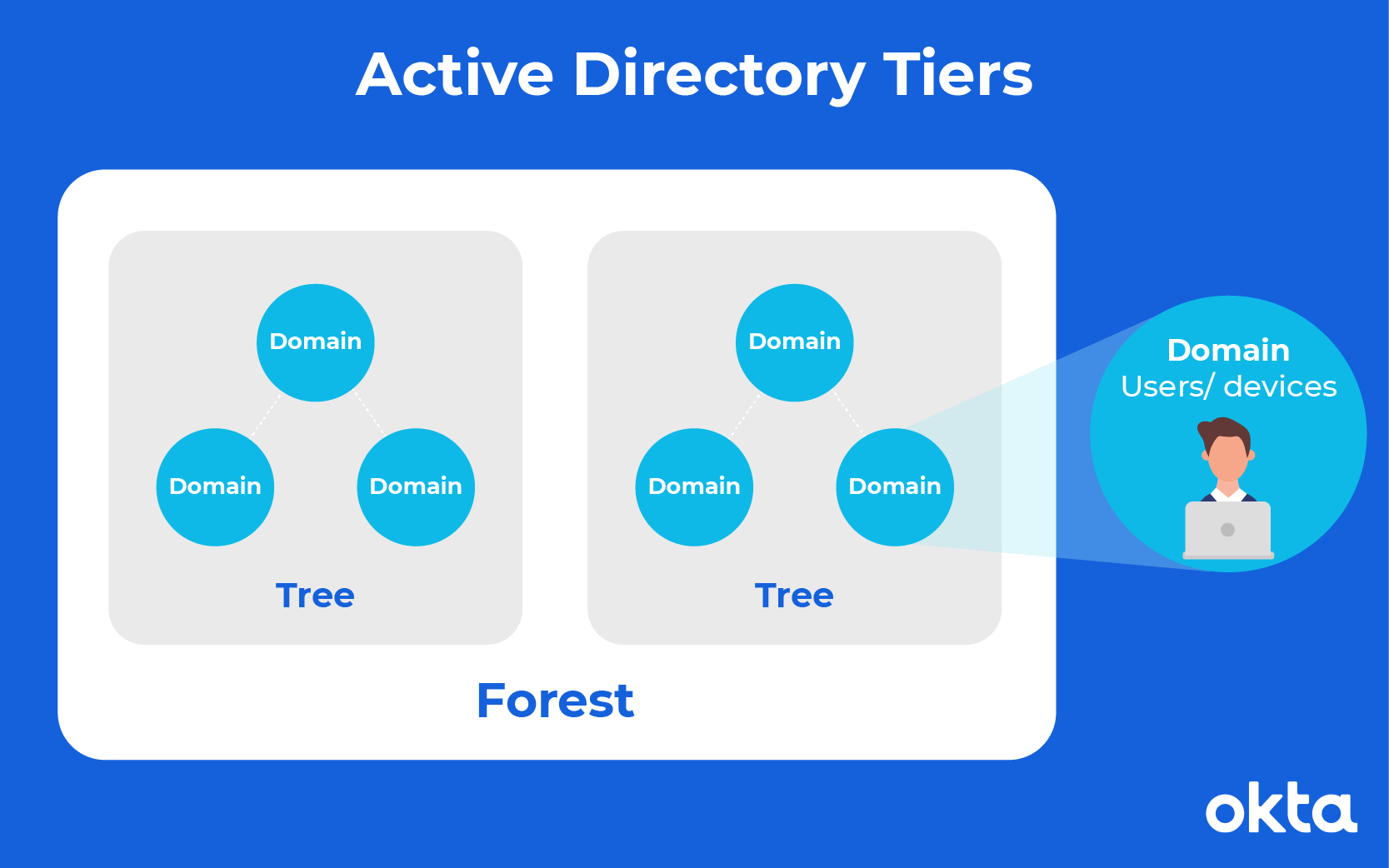
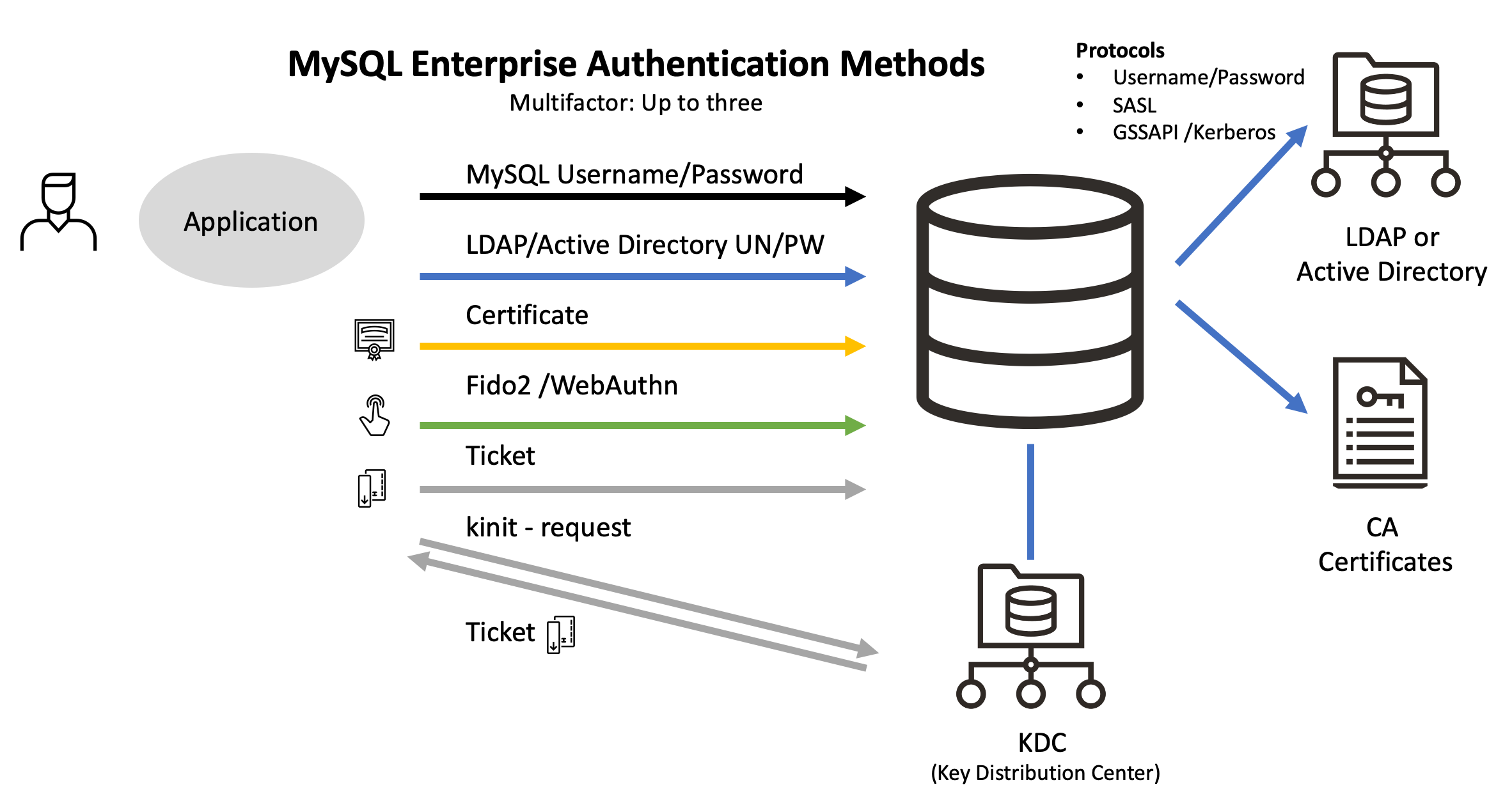
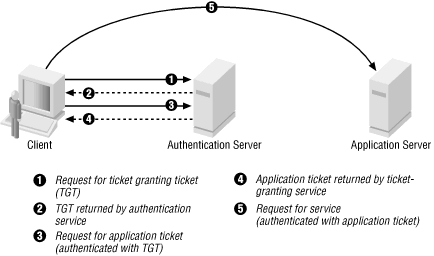
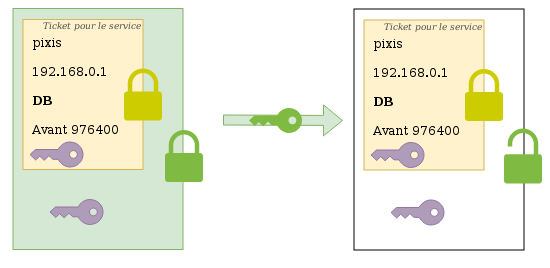
How Windows Authentication for Azure SQL Managed Instance is implemented with Azure AD and Kerberos - Azure SQL Managed Instance | Microsoft Learn

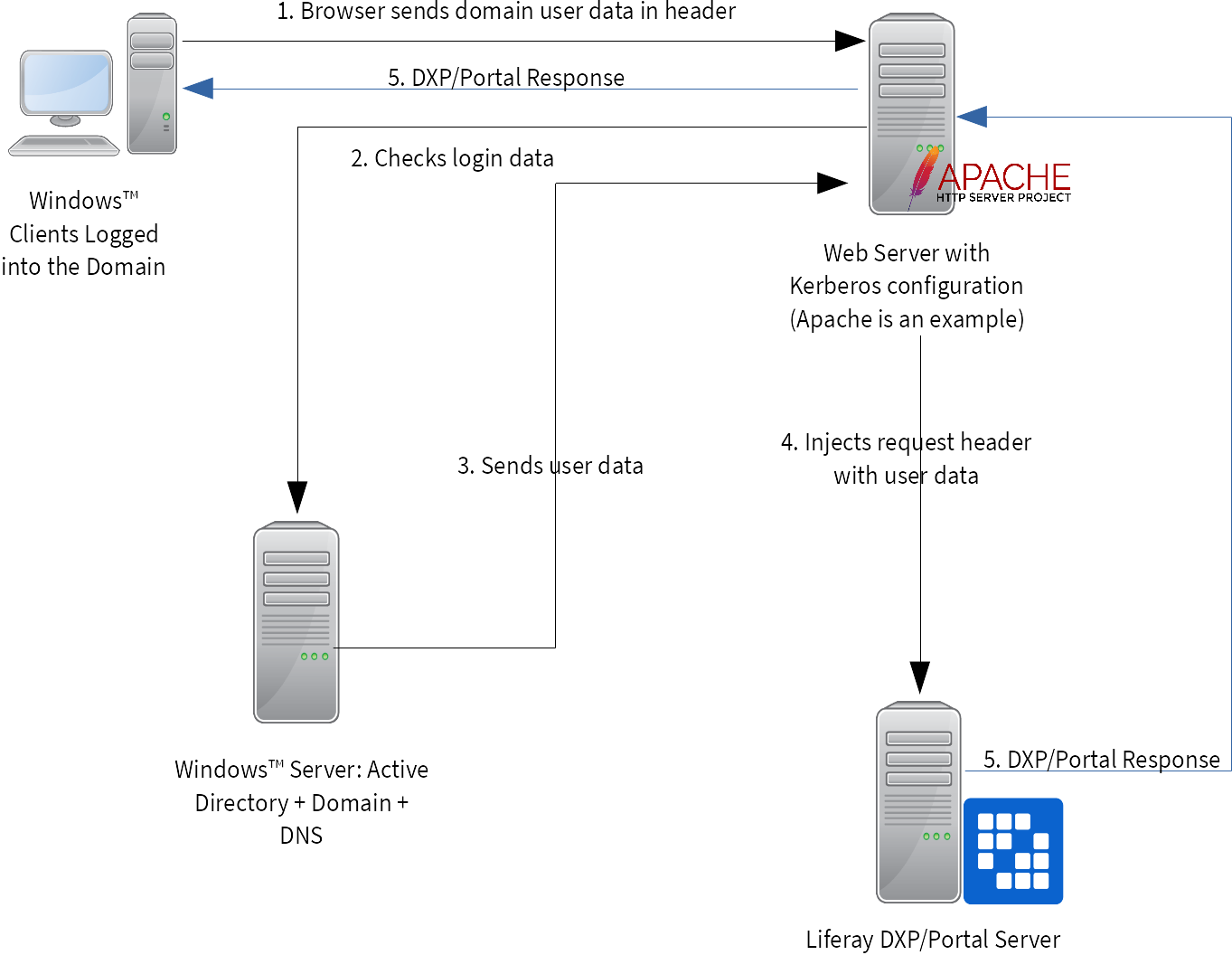
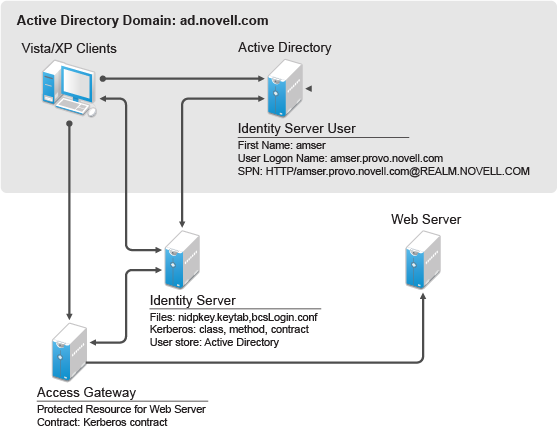
Novell Doc: Novell Access Manager 3.0 SP4 Administration Guide - Configuring Kerberos for Authentication